Millions trust browser extensions without realizing they could be a serious security risk.
Just a cute little puzzle piece, right?
For Chrome, as well as other browsers, extensions are represented as a harmless jigsaw puzzle piece, as if to represent that it builds out the functionality of your browser. This imagery is somewhat misleading as browser extensions don’t just build outward, but downward. That is, browser extensions rely on permissions to function, and these permissions can be surprisingly invasive and misused to put you at risk. Let’s look at some examples.
You want to see my what?!
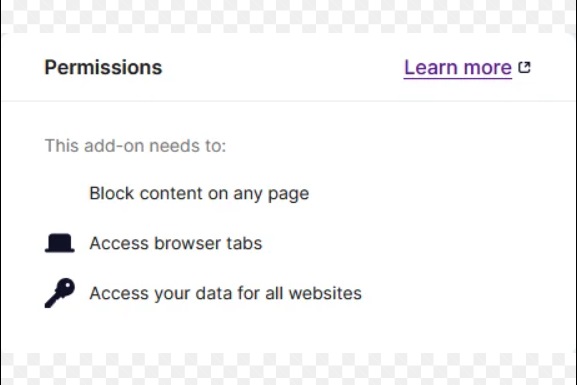
How would you feel about giving a stranger the following permissions?
- Permission to read and change the webpages you visit
- Permission to access your clipboard
- Permission to log your keystrokes
- Permission to read your cookies
Depending on what browser extensions you have installed, you may already be doing this.
Do you have a browser extension for an ad blocker or grammar checker? They are likely reading your webpages. How else would you expect them to recognize ads on pages you visit or insert a green squiggly underline when you write “their” instead of “they’re”? The extension has to see your webpage to do its job.
How about a copy-paste manager or translation extension? They might have visibility of the contents of your clipboard – I hope you don’t have anything sensitive such as passwords stored in there.
Perhaps you have a note-taking add-on, or if you’re visually impaired you have a screen reader for accessibility purposes? Those extensions could be logging your keystrokes. Just go ahead and type your bank number and password, it’s probably fine.
If you’re using a password manager browser extension, it may be reading your cookies to determine whether or not you are already logged into a specific site. This means that it could see which sites you visit and for how long.
Aren’t you going to at least buy me dinner first?
So what? I choose to give up a bit of privacy for convenience
The examples above are the best-case scenarios, where a browser extension is using these permissions responsibly to function as expected. However, there are two risks:
Purposely Malicious Browser Extensions
Some bad actors may release browser extensions with the sole intent of abusing these permissions. For example, an attacker released a “ChatGPT for Google” extension which was based on functional, open-source code. The extension worked as advertised but it also harvested Facebook session tokens (you let it read your cookies, remember?), which allowed the attacker to bypass 2FA and login to victims’ Facebook accounts. Is that really such a big deal? Absolutely. An attacker could change your password to lock you out, view private chats and use that as blackmail, and run fraudulent ads and link them to your account (enjoy your Facebook ads bill).
Doesn’t Google vet new extensions? Yes, but there are hundreds of thousands out there and some will slip through the cracks. Attackers use techniques such as delayed activation and code obfuscation to sneak by. They may also originally release a harmless app to get through the initial screening process, and then months later update it with malicious code after it has been installed by users.
Compromised Browser Extensions
Even well-intentioned and honest browser extensions could be a serious threat. Many popular add-ons are developed and maintained by individuals or small teams who may not have a cybersecurity expert on-staff. As a result, they are at risk of becoming compromised, which has happened an alarming number of times.
Think about it: a browser extension is a very attractive target for an attacker. They are already installed on browsers and trusted by users. Through a compromised browser extension, an attacker could abuse the permissions for malicious purposes and siphon user data.
Reader Mode is an example of a web extension that was compromised through a phishing attack. They were transparent about what happened, how their users were impacted, and their response.
Abandoned browser extensions, of which there are more than 100,000, are also a problem. Users may have installed them years ago, forgotten about them, and the developer no longer supports or patches them. These vulnerable add-ons can be hijacked and provide a backdoor to your browser.
Even modern and sophisticated browser extensions can be risky. Just last week, multiple password manager web extensions were revealed to have vulnerabilities where an attacker could steal credentials and credit card information.
What should I do?
As an individual user, the simple answer is to uninstall browser extensions that you don’t need and avoid installing unnecessary ones in the future. For the ones you decide to keep, check what permissions you are granting and which sites they can access, and consider if the risks outweigh the benefits.
From a business perspective, the answer isn’t so simple. Most standard tools such as antivirus and endpoint detection & response (EDR) are not designed to have visibility of browser extensions, their permissions, and how they are being used or abused. This means that companies have limited visibility and controls on what extensions their employees have added to their browser – the same browser they use to login to business-related cloud portals and web services.
One solution is to use mobile device management (MDM) tools such as Microsoft InTune to lock down browser extensions (with compatible browsers). The advantage with this approach is that it is configured as a Group Policy, meaning that it could be deployed top-down so that each individual workstation would not need to be touched.
If you’re a small business and don’t yet have a team to keep you up to date with cybersecurity best practices, such as deploying MDM to safeguard your devices, contact EMKAL. We would be happy to chat about your current IT challenges and how we might be able to help!


